Responsible Vulnerability Disclosure
CIRCL, with its role as a CERT, receives reports about new vulnerabilities in software and hardware products or discovers them itself. The process of responsible vulnerability disclosure is described in the document to ensure an adequate collaboration with the vendors and/or the reporters. The two main objectives of the procedure are to get the vulnerability corrected and to ensure a safe notification to the users or customers at the end of the overall process.
Overview
Security vulnerabilities exist in any software or hardware implementation. Responsible vulnerability disclosure is a required process to fix and improve the security of software or hardware used.
Steps
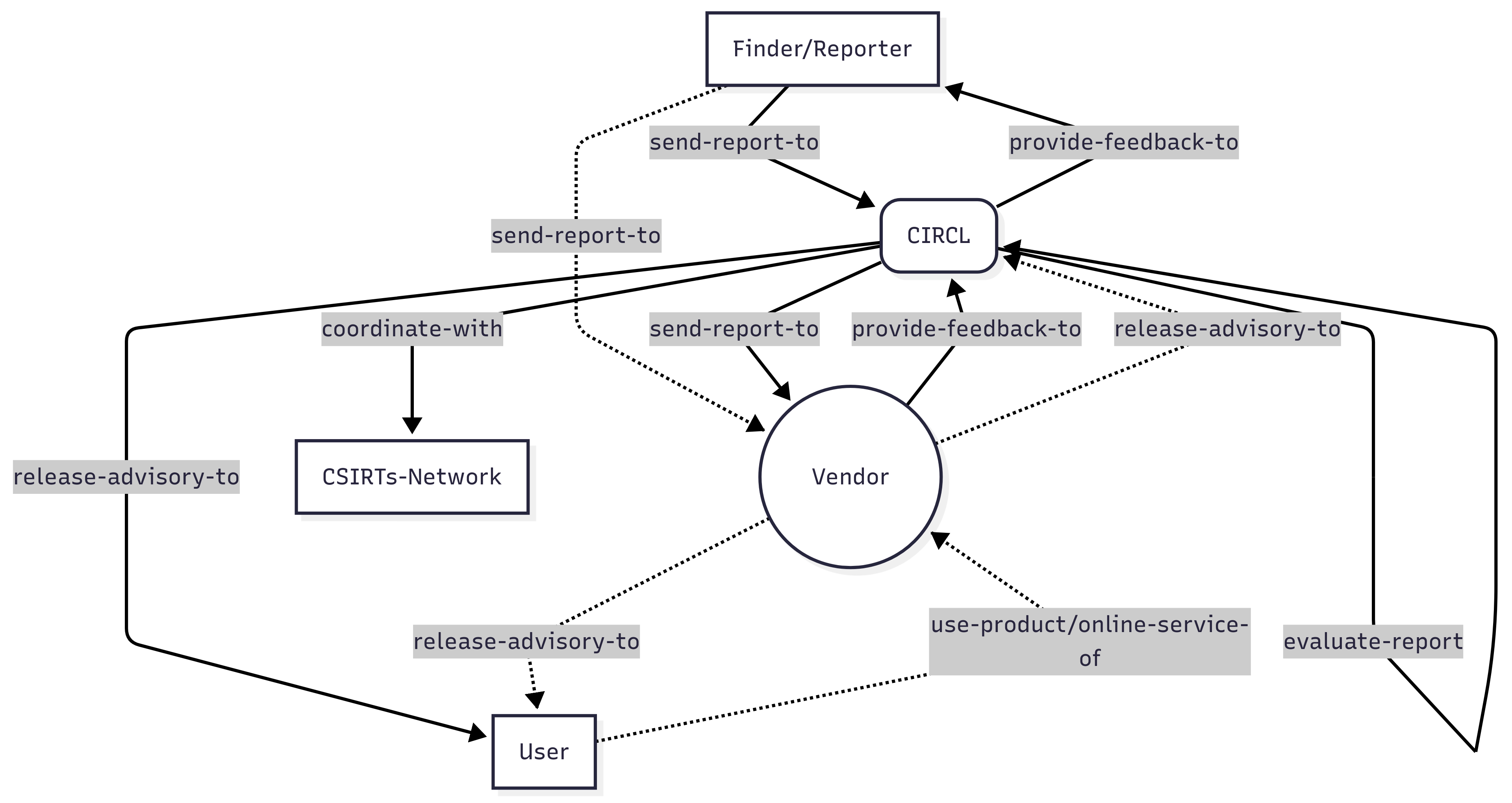
Vulnerability notification to CIRCL
CIRCL can receive vulnerability notifications from named or anonymous reporters. In some cases, CIRCL discovers the vulnerability within the frame of a specific incident analysis or report. Notifications can only be received by the standard report process of CIRCL. The use of PGP is recommended while exchanging information about the vulnerability. CIRCL expects from the reporter a clear statement whether they want to remain anonymous. By default, the reporter will be mentioned to the software or hardware vendor.
CIRCL expects from the reporter a reasonable effort to ensure that the report is complete and includes enough information for the vendor to evaluate the vulnerability report.
Notification to the vendor by CIRCL
If the vulnerability report is complete, CIRCL (as coordinator or reporter) notifies the vendor via the available security channels. This notification is considered as the initial notification. The default delay for the vendor to resolve the vulnerability is 30 days starting from the initial notification. If the vendor cannot fulfill within the 30 days period, the vendor must provide to CIRCL an explanation why he cannot correct the vulnerability within that time frame. Under such a condition, additional grace period can be requested. CIRCL and/or the reporter will review the explanation and CIRCL will find an agreement with the vendor if possible. A request to CVE assignment is done at NIST by CIRCL if the vendors is not known to have an existing CVE assignment procedure.
Publication by the vendor
If the grace period is over, the vendor publishes the vulnerability including patches or updates to correct the vulnerability. The publication can be done via the official public vendor channels or via security channels.
Publication by CIRCL or/and the reporter
If the grace period is over and the vendor doesn’t provide an acceptable answer, CIRCL and/or the reporter will publish the information of the vulnerability.
References
Revision
- version 1.0


