Overview
Allaple worm family has been discovered in late 2006. The Allaple worm is a polymorphic malware designed to spread over Local Area Network and Internet. The worm was designed by a dissatisfied customer of an insurance company in order to DDoS some websites in Estonia. CERT-FI described in 2007 how to detect and identify Allaple variants on the network via ICMP packets generated by the malware. By analyzing blackhole data close to RFC1918 networks , CIRCL discovered a significant persistence of this worm family in Local Area Networks.
Statistics
As the monitoring is performed on black hole networks sensors focusing on typographic errors in RFC1918 ranges, the detected infections, in the below statistics, are much lower (by a factor of 10 at least) than the real infections present in Local Area Networks who don’t leak towards the Internet. raw data
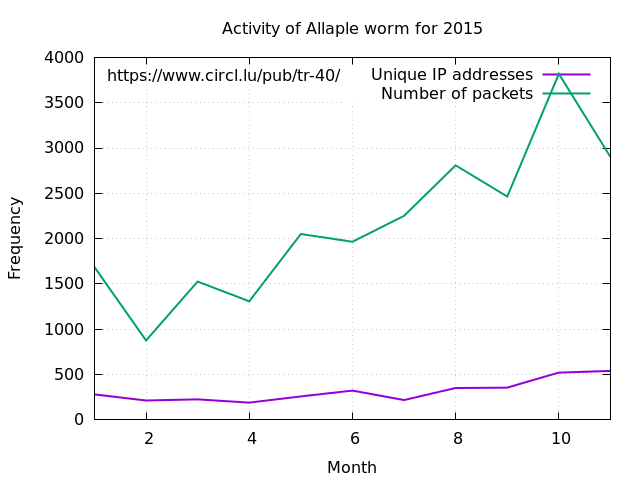
2015
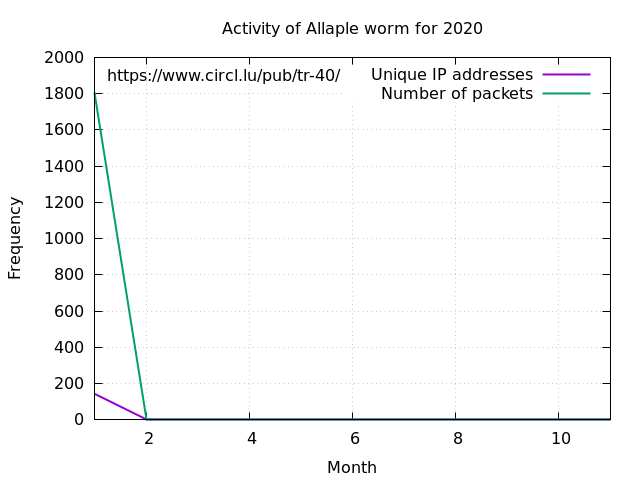
2017
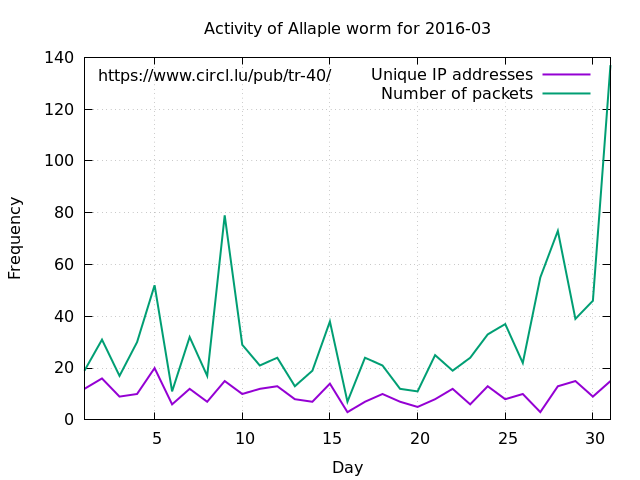
March 2016
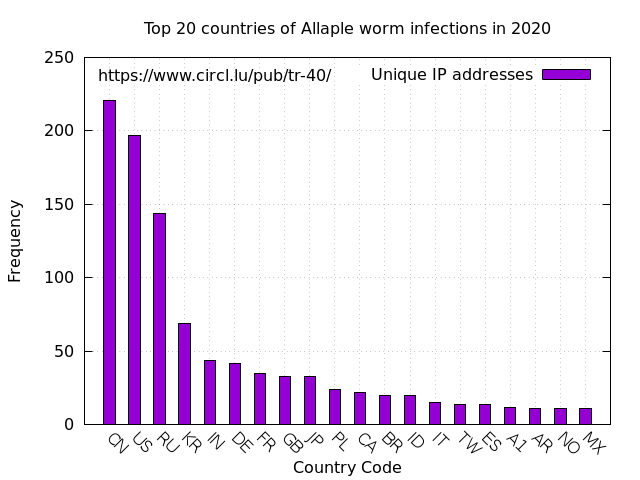
Top 20 countries
Malware
Allaple worm is regularly sending ICMP packets to various IP addresses calculated. The string payload sent in the ICMP is “Babcdefghijklmnopqrstuvwabcdefghi”. This artefact was used in order to detect the infected systems sending these ICMP packets towards the black hole networks monitored.
1 Addend = 0; 2 dword_41CE2C = (GetTickCount() % 0xFF) << 16; 3 do 4 { 5 if ( Addend >= 0xFFF8 ) 6 break; 7 while ( dword_41CE4C ) 8 Sleep(0x2710u); 9 v1 = dword_41CE2C | dword_41CE28 | *(dword_41CE34 + 2 * Addend); 10 InterlockedIncrement(&Addend); 11 lpParameter = _byteswap_ulong(v1); 12 v2 = CreateThread(0, 0x500u, sub_403970, lpParameter, 4u, &ThreadId); 13 ...
1 signed int __stdcall sub_403BF0(int a1) 2 { 3 int v1; // eax@4 4 signed int result; // eax@9 MAPDST 5 int hIcmpFile; // [sp+Ch] [bp-9Ch]@2 6 signed int i; // [sp+10h] [bp-98h]@3 7 CHAR ICMP_string; // [sp+18h] [bp-90h]@3 8 int IcmpReplyBuffer; // [sp+40h] [bp-68h]@4 9 int v8; // [sp+44h] [bp-64h]@5 10 11 if ( icmp_functions_initialized ) 12 { 13 hIcmpFile = IcmpCreateFile(); 14 if ( hIcmpFile ) 15 { 16 result = -1; 17 lstrcpyA(&ICMP_string, aBabcdefghijklm); 18 for ( i = 2; i; --i ) 19 { 20 v1 = lstrlenA(&ICMP_string); 21 if ( IcmpSendEcho(hIcmpFile, a1, &ICMP_string, v1, 0, &IcmpReplyBuffer, 100, 2000) ) 22 { 23 IcmpParseReplies(&IcmpReplyBuffer, 100); 24 if ( !returnStatus ) 25 result = 0; 26 } 27 } 28 IcmpCloseHandle(hIcmpFile); 29 } 30 else 31 { 32 result = 0; 33 } 34 } 35 else 36 { 37 result = 0; 38 } 39 return result;
Recommendations
The following Snort IDS rule can be used to detect internal systems infected with Allaple malware family:
alert icmp $HOME_NET any -> $EXTERNAL_NET any (msg:"ET WORM Allaple ICMP Sweep Ping Outbound"; icode:0; itype:8; content:"Babcdefghijklmnopqrstuvwabcdefghi"; threshold: type both, count 1, seconds 60, track by_src; classtype:trojan-activity; reference:url,www.sophos.com/virusinfo/analyses/w32allapleb.html; reference:url,isc.sans.org/diary.html?storyid=2451; sid:2003292; rev:6;)
Infected IP addresses
CIRCL notified the responsible CERT,CSIRT and/or abuse point of contact about the potential infected systems in their Local Area Networks.
References
- https://www.f-secure.com/v-descs/allaple_a.shtml
- http://isc.sans.org/diary.html?storyid=2451
- http://www.sophos.com/virusinfo/analyses/w32allapleb.html
Acknowledgment
CIRCL would like to thank the Foundation Restena for their collaboration in the blackhole research topic.
Classification of this document
TLP:WHITE information may be distributed without restriction, subject to copyright controls.
Revision
- Version 1.2 June 9, 2017 Statistics for 2017 and links to raw data (TLP:WHITE)
- Version 1.1 March 21, 2016 Statistics for 2015 and 2016 updated (TLP:WHITE)
- Version 1.0 September 24, 2015 Initial version (TLP:WHITE)


