Abstract
This article exposes how cyber-threats indicators sharing platforms, such as the Malware Information Sharing and Threat Sharing Platform (MISP), can help all actors involved in information security and data protection within Europe in fulfilling their obligations under the future General Data Protection Regulation (GDPR) to apply in the European Union (EU). Although such kind of platform could be used in order to share personal data, the reason why such data is exchanged should be perceived as being within the legitimate interest of data controllers and the interest of the individuals whose data is being shared, therefore in line with the requirements of the GDPR.
Introduction
The GDPR is the new European data protection framework1. As a regulation, it will be binding in its entirety and directly applicable in all Member States from 25 May 2018. This Regulation contains many clear obligations for all actors implied in personal data management - which consists in the management of data of identified or identifiable individuals.
In the field of information security, experts responsible for the security and integrity of information systems will seek patterns related to compromised systems, such as but not limited to a specific but not normal ongoing communication traffic on the Internet incoming from a compromised computer. Such signatures of compromising software or characterising a compromised computer can be found in many different forms, and are regrouped under the term Indicators of Compromises of targeted attacks (IoCs).
Platforms like the Malware Information Sharing and Threat Sharing Platform (MISP) dedicated to the sharing of cyber security threats, IOCs and financial fraud indicators can help concerned actors in fulfilling their obligations under the GDPR, especially regarding their clear responsibility of securing any information systems hosting personal data under their responsibilities. Moreover, the legal and regulatory framework introduced by this new Regulation can often be perceived as a challenge by information security experts.
1 - What is MISP
The Malware Information Sharing and Threat Sharing Platform2 (MISP) is a software for sharing, storing and correlating indicators of compromises of targeted attacks, cyber-security threats and financial fraud indicators, among which MD5 Hashes (a signature of code used to verify data integrity), threat actor names and Bitcoins addresses.
MISP allows organisations fighting cyber-threats to share information about ongoing malware activities and their relative indicators, which can greatly improve the set-up of countermeasures meant to be used against targeted attacks. MISP is therefore an essential tool in setting-up preventive actions and detection and as such a necessary information source for pre-emptive monitoring of threats and potential leaks.
Like most community-driven projects, MISP is an Free Software platform, licensed under the Affero GNU GPL v3. Therefore, all users of MISP are free to use, distribute, modify and distribute modifications of the source code which is freely available, as long as they comply with the licensing terms. This allows any users of MISP to audit the platform for security reasons, among other needs.
Thus, MISP is to be considered as an important tool to ensure efficient network and information security. Several actors are accountable for such data security and related information system under the GDPR.
Communities of information sharing are built on tools like MISP. CIRCL as a CERT (Computer Emergency Response Team/Computer Security Incident Response Team) for the private sector, communes and non-governmental entities in Luxembourg created and operates several communities to automate information sharing at national, European and international levels.
2 - Threat information sharing as an essential security activity for all actors implied in personal data protection
At the time of writing this paper, the processing of personal data is regulated at the EU level under the Data Protection Directive 95/46/EC. As a directive, this instrument had to be implemented in each EU Member State. The drawback of a directive is that inevitable differences have arisen across Member States in certain areas, raising legal uncertainty due to the heterogeneous implementations. This has made it difficult for companies that operate across the EU to adopt a common compliance framework in all relevant Member States.
The GDPR clarifies the roles and responsibilities of many actors dealing directly or indirectly with data protection topics (i.e. national regulatory bodies and EU level activities).
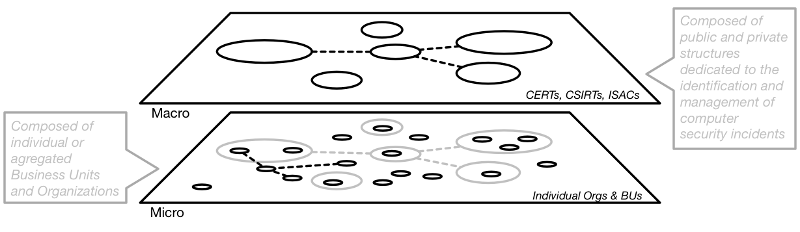
In order to ensure state-of-the-art security, threat information sharing should be perceived as a necessary action in the framework of the GDPR for all of these actors, should they be at a micro (i.e. within companies and organisations or as subcontracting data-processors) or at macro level (i.e. at the level of organisation dedicated to provide resources for gathering information on cyber threats and coordinate computer security incident responses).
As illustrated in the above Figure, each of these levels relies on its specific networks of cyber threats information exchanges. A close co-operation between these two levels is clearly required in order to ensure the optimal diffusion of knowledge required in order to keep information systems secured.
2.a - Micro-level (distinctive organisation and business unit level)
By micro-level, the author refers to the level of distinctive organisation, managing in some way or another personal data, either for themselves, as data controllers or for the benefit of third parties, as data processors.
The processing and control of personal data by any organisation in order to achieve efficient physical and organisational information security (including personal data) is not only legitimate but required under the GDPR. Achieving an efficient evaluation and treatment of threats and related risks on data is a legitimate interest, which data controllers are accountable for: “Taking into account the state of the art, the costs of implementation and the nature, scope, context and purposes of processing […], the controller and the processor shall implement appropriate technical and organisational measures to ensure a level of security appropriate to the risk […] [including a] process for regularly testing, assessing and evaluating the effectiveness of technical […] measures for ensuring the security of the processing” [Art. 32, 1., d) GDPR].
Such evaluation and management of information security-related threats and risks require an optimisation of information-gathering techniques. Within a given organisation, the data controller will be responsible and accountable for using state of the art security, and a complementary data protection Officer might also be required with appropriate knowledge on this topic. Myopia due to core business activities focus might restrain the ability of such organisations to achieve an efficient monitoring of ongoing threats and risks impacting their information systems and the data contained herein.
MISP, by permitting the access of accountable actors to a threat-sharing platform, has to be perceived as an essential tool in order to resist to actions that violate the availability, authenticity, integrity and confidentiality of stored personal data. Such facilitation constitutes a step forward in the interest of the individual whose data is being shared.
MISP also helps data controllers to fulfil security proactive obligations (both technological and organisational), as referred to in recital (87) GDPR ”[i]t should be ascertained whether all appropriate technological protection and organisational measures have been implemented to establish immediately whether a personal data breach has taken place and to inform promptly the supervisory authority and the data subject.”
Under the GDPR, data controllers need to prepare themselves for security issues and breaches. This requires a proactive procedure in order to ensure that threats are accordingly mitigated. Article 6, 1., (c) GDPR clarifies the lawfulness of such processing. Since all data controllers will face security obligations, the ”[p]rocessing shall be lawful only if and to the extent […] [it] is necessary for compliance with a legal obligation to which the controller is subject”. Information systems’ security is clearly a legal obligation for all data controllers and processors across the EU.
2.b - Macro-level (Cyber-security Organisations, CSIRTs and CERTs)
By macro-level, the author refers to the networking of information exchange abilities of Computer Emergency Response Teams (CERTs), Computer Security Incident Response Teams (CSIRTs) and Information Sharing and Analysis Centers (ISACs).
The security of personal data of information systems relies strongly on external actors, having access to specific security information flows and related communities, and more largely any providers of security technologies and services. Those actors are often confronted with a need to deal with personal data, for instance in case of a data leak unnoticed by the initial data controller. The GDPR clarifies the situation for such actors dedicated to technical and organisational information security, by underlining the fact that personal data processing to the interest of the data security is clearly a legitimate interest for data controllers: “The processing of personal data to the extent strictly necessary and proportionate for the purposes of ensuring network and information security, i.e. the ability of a network or an information system to resist, at a given level of confidence, accidental events or unlawful or malicious actions that compromise the availability, authenticity, integrity and confidentiality of stored or transmitted personal data, and the security of the related services offered by, or accessible via, those networks and systems, by public authorities, by computer emergency response teams (CERTs), computer security incident response teams (CSIRTs), by providers of electronic communications networks and services and by providers of security technologies and services, constitutes a legitimate interest of the data controller concerned […].” [Recital (49) GDPR].
Of course, this does not omit a need of a clear balancing test in between the interests of all involved actors, with a strong focus on trust on how data will be used by organizations connected to information security threats-sharing platforms. MISP for example includes a strong enforcement of the traffic light protocol, assigning a strong confidentiality level to data being shared. Such confidentiality options are the balanced way chosen in order to protect the individual’s interests.
Moreover, as stated in the article 2, 2.,(d) GDPR ”[t]his Regulation does not apply to the processing of personal data: […] (d) by competent authorities for the purposes of the prevention, investigation, detection or prosecution of criminal offences or the execution of criminal penalties, including the safeguarding against and the prevention of threats to public security”. Therefore, depending on the public mandate of CERTs, CSIRTs and ISACs, should such organisations have a clear institutional role in detecting cyber criminal offences, personal data exchange for this purpose is not to be considered as specifically restricted by the GDPR. This exception however will definitively not apply to all CERTs and connected organisations.
Conclusion
Creating adequate tools in order to ensure the security of information systems requires a lot of information to be exchanged in between many different actors. Individual organisations acting as data controllers, organisations dedicated to cyber incident and computer security management, but also national data protection authorities (NDPAs) all require up-to-date and clear information within their respective roles dedicated to the protection of personal data. All of these actors should also enforce a process of active monitoring of ongoing cyber-threats. In such condition, IoCs sharing platforms like MISP are essential.
Furthermore, the GDPR creates a new European Data Protection Board (EUDPB), to replace the Working Party referred to in article 29 of the directive 95/46/EC and clarifies its operational obligations in terms of reporting to the EU Commission and Parliament. Since the EUDPB will be in charge of, among other things, cross-border data transfer outside of the EU, EUDPB could use IoCs sharing platforms in order to monitor potential leaks and new threats to which EU personal data might be exposed.
Important legal grounds regarding the protection of personal data are not only in favour of IoCs information sharing, and platforms such as MISP are an essential tool in order for the actors implied in data protection to fulfil their duties.
Footnotes
1: The demonstration hereafter exposed is mainly based on the General Data Protection Regulation, as described in the Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data, and repealing Directive 95/46/EC, O.J.E.U., L 119/1 of 4th of May 2016.
2: http://www.misp-project.org/
References
- Incident Response: Protecting Individual Rights Under the General Data Protection Regulation - Andrew Cormack, “Incident Response: Protecting Individual Rights Under the General Data Protection Regulation”, (2016) 13:3 SCRIPTed 258 https://script-ed.org/?p=3180 DOI: 10.2966/scrip.130316.258
Contact
If you have any question or suggestion about this topic, feel free to contact us.
Classification of this document
TLP:WHITE information may be distributed without restriction, subject to copyright controls.
Revision of the text
- Version 1.1 - 7 March 2017 - TLP:WHITE
- Version 1.0 - 10 February 2017 - TLP:WHITE
Preliminary versions
A preliminary version of this article will be published in next LegiMag, as published by Legitech in Luxembourg (Title of article: Security-related actionable information and future of Personal Data Protection in the EU, Author: M. Farcot). Further information on publication will be added when received.


