Description
Many Microsoft Exchange Servers are left unmaintained, when it comes to patching them with the latest security updates. This introduces an enormous risk for the companies using those servers.
The main risks are: - a potential compromise of the server - accessing of private, confidential and/or business related data by third parties - unwanted modification or deletion of data - exfiltration of data - lateral movement and infection of other parts of the infrastructure - financial loss through blackmailing - productivity and financial loss by re-installing the infrastructure - reputation loss
Unfortunately, it is not uncommon to end up with a compromised Exchange server. We have seen countless cases in the last years. Vulnerabilities in Exchange are quite frequent and most of the time they have a high CVSS. Remote Code Execution Vulnerabilities are patched every few months. If these vulnerabilites are not patched by the updates of Microsoft or otherwise mitigated, there is a severe risk of the server being rapidly compromised.
Updating servers is a critical task that is either often completely forgotten, or the procedures for updating are incomplete. Especially professional integrators seem to commit systematic mistakes in this regard. From our experience, it frequently happens that whilst the auto-updating of Exchange servers and Operating systems are enabled, it seems to be a less known fact that mandatory cummulative updates have to be applied manually. If not done, the server will forever remain unpatched, with a potentially vulnerable version of Microsoft Exchange.
CIRCL invests a lot of time to assess the situation in Luxembourg and identifies the owners of the servers or the IP addresses where such unpatched server run and once identified, informing the technical point of contact. One could assume the scenario would end here, with the technical point of contact being informed and the information being relayed by them to the corresponding teams or people who would then patch the vulnerable servers shortly after. Unfortunately, reality paints a darker picture. We see a lot of delay and unresponsiveness, while we also deal with compromised servers - where we have notified the owners repeatedly before.
Some organisations are compromised for a long time without ever noticing it.
To illustrate the problem, we collected metrics about the situation in Luxembourg.
The data is from 21 February 2023, one week after the last patches have been released by Microsoft, patching several Remote Code Execution vulnerabilities. We are looking at 533 servers which haven’t been updated to the latest February 2023 patch after one week. The oldest unpatched installations haven’t been patched for 22 months.
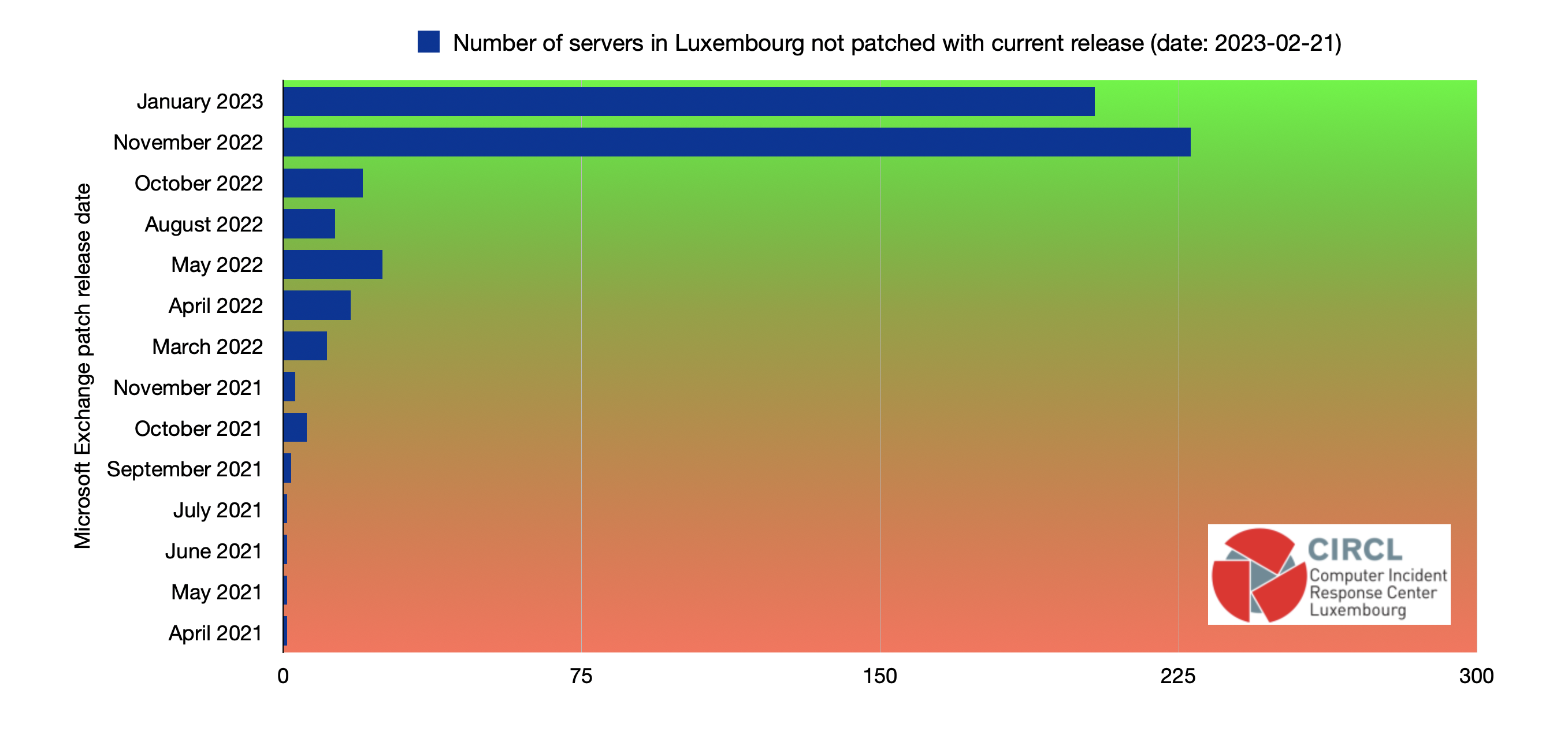
All 533 servers are currently at stake and need immediate attention. This is an alarming situation and should be addressed by all responsible people working with Exchange servers.
If your organisation needs support in assessing the current threat for your infrastructure, don’t hesitate to get in contact with us.
Recommendations
- If you’re running your own infrastructure: manually check if the currently running version is the most recent, if not, apply upgrades.
- If you have a service provider that is supposed to take care about the security updates: ask them to report the installed version and the most recent version available. If there’s a discrepancy, insist on the upgrade. Ask for monthly status, review current contracts if necessary.
References
- Exchange Server build numbers and release dates
- TR-70 - Vulnerabilities in Microsoft Exchange CVE-2022-41040 - CVE-2022-41082
- TR-64 - Exploited Exchange Servers - Mails with links to malware from known/valid senders
Classification of this document
TLP:CLEAR information may be distributed without restriction, subject to copyright controls.
Revision
- Version 1.1 - TLP:CLEAR - added recommendations - 22nd February 2023
- Version 1.0 - TLP:CLEAR - First version - 21st February 2023


