Microsoft researchers focusing on industrial control system found a significant number of vulnerabilities in CODESYS V3 software development kit which is used in multiple industrial devices such as programmable logic controllers (PLC).
Affected Products
- all versions of CODESYS V3 prior to version 3.5.19.0
All variants of the following CODESYS V3 products in all versions prior V3.5.19.0 containing at least one of the components CmpApp, CmpAppBP, CmpAppForce, CmpFiletransfer or CmpTraceMgr are affected, regardless of the CPU type or operating system:
- CODESYS Control RTE (SL)
- CODESYS Control RTE (for Beckhoff CX) SL
- CODESYS Control Win (SL)
- CODESYS Control Runtime System Toolkit
- CODESYS Safety SIL2 Runtime Toolkit
- CODESYS Safety SIL2 PSP
- CODESYS HMI (SL)
- CODESYS Development System V3
- CODESYS Development System V3, the simulation runtime is also affected
In addition, the following products based on the CODESYS Control V3 Runtime System Toolkit are affected in all versions prior to V4.8.0.0:
- CODESYS Control for BeagleBone SL
- CODESYS Control for emPC-A/iMX6 SL
- CODESYS Control for IOT2000 SL
- CODESYS Control for Linux SL
- CODESYS Control for PFC100 SL
- CODESYS Control for PFC200 SL
- CODESYS Control for PLCnext SL
- CODESYS Control for Raspberry Pi SL
- CODESYS Control for WAGO Touch Panels 600 SL
Vulnerabilities
| Vulnerabiloty | CODESYS Component Impacted |
|---|---|
| CVE-2022-47379 | CMPapp |
| CVE-2022-47380 | CMPapp |
| CVE-2022-47381 | CMPapp |
| CVE-2022-47382 | CmpTraceMgr |
| CVE-2022-47383 | CmpTraceMgr |
| CVE-2022-47384 | CmpTraceMgr |
| CVE-2022-47385 | CmpAppForce |
| CVE-2022-47386 | CmpTraceMgr |
| CVE-2022-47387 | CmpTraceMgr |
| CVE-2022-47388 | CmpTraceMgr |
| CVE-2022-47389 | CMPTraceMgr |
| CVE-2022-47390 | CMPTraceMgr |
| CVE-2022-47391 | CMPDevice |
| CVE-2022-47392 | CmpApp/ CmpAppBP/ CmpAppForce |
| CVE-2022-47393 | CmpFiletransfer |
Remediation
Patches have been released to address this vulnerability by CODESYS.
Recommendations
- Limit access to industrial control systems with at least network packet filtering to limit network exposure
- Update/Upgrade the software components immediately and generally keep the infrastructure up-to-date
- Review logs and check system integrity
Notifications
CIRCL (Computer Incident Response Center Luxembourg) sends notifications to ISPs and known contact points when publicly exposed vulnerable devices were discovered. If you would like to directly share your IP resources for notifying the appropriate contact point, please reach out to us.
Luxembourg
While industrial systems ideally should remain private, it’s worth noting that there are certain exposed interfaces in Luxembourg.
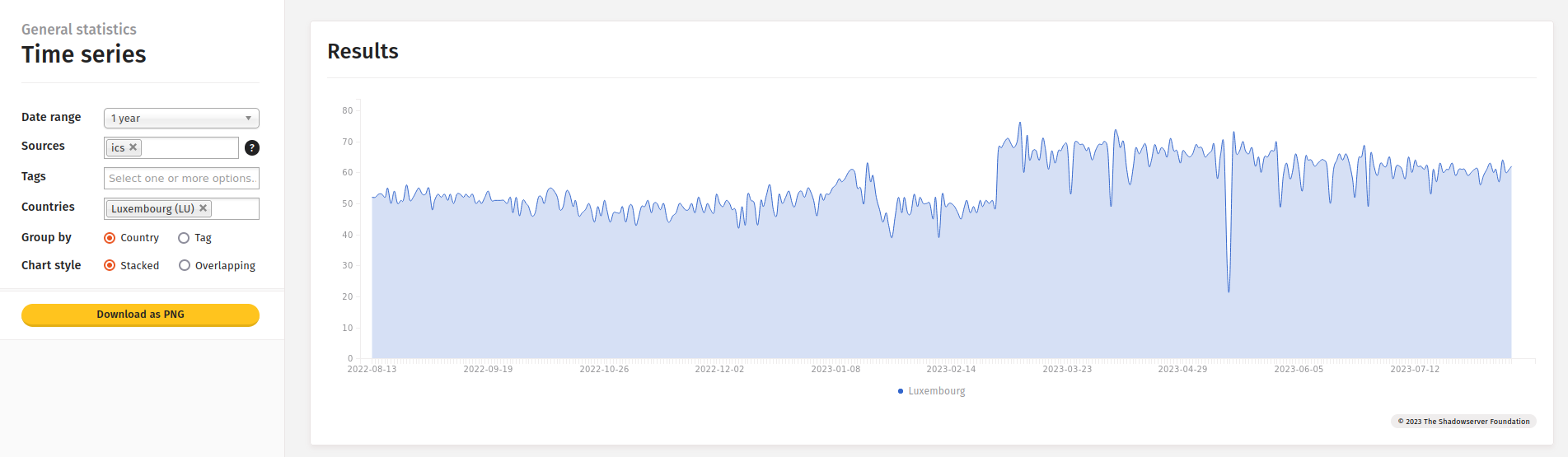
Statistics from ShadowServer dashboard
References
- [Vendor] - CODESYS Advisory 2023-02
- [Reporter] - Multiple high severity vulnerabilities in CODESYS V3 SDK could lead to RCE or DoS
- [Reporter] - Microsoft ICS Forensics Framework
Classification of this document
TLP:CLEAR information may be distributed without restriction, subject to copyright controls.
Revision
- Version 1.0 - TLP:CLEAR - First version - 14th August 2023


